A sophisticated Russian state-sponsored cyber campaign has targeted prominent academics and critics of Russia through an innovative social engineering attack that exploited Google’s Application Specific Password (ASP) functionality.
The operation, which ran from April through early June 2025, demonstrated a creative approach to gaining persistent access to victim email accounts by impersonating official U.S. Department of State communications.
The threat actors employed extensive rapport-building techniques and highly customized lures to establish trust with their targets before launching the credential harvesting phase.
Rather than relying on traditional malware deployment, the attackers focused on manipulating victims into voluntarily creating and sharing ASP credentials, which are 16-character randomly generated passcodes designed to allow third-party applications access to Google accounts.
Google Threat Intelligence analysts identified this activity as UNC6293, assessing with low confidence that the group is associated with the well-known APT29/ICECAP threat cluster.
The researchers noted that attackers specifically targeted high-value individuals in academic and policy circles who frequently criticize Russian government actions, suggesting a clear intelligence collection motive.
The campaign’s impact extended beyond simple credential theft, as ASPs provide persistent access to email accounts without requiring traditional authentication methods.
Google Threat Intelligence Group confirmed that multiple Gmail accounts were compromised through this technique, though the company has since re-secured all affected accounts.
The operation’s sophistication lies in its exploitation of legitimate security features rather than technical vulnerabilities.
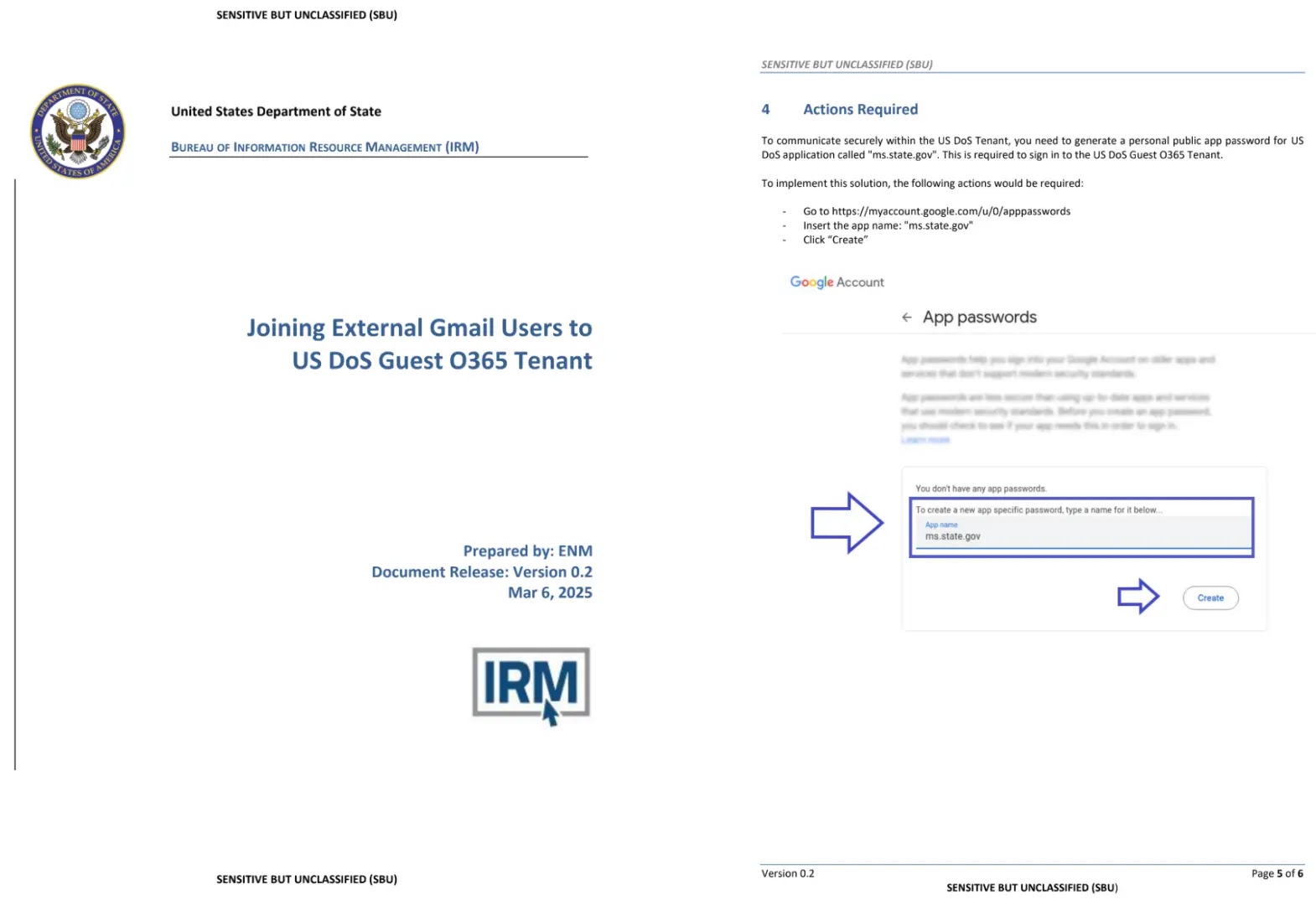
Two distinct campaigns were observed, with the first suggesting victims use “ms.state.gov” as their ASP name, while the second employed Ukrainian and Microsoft-themed naming conventions.
Prominent British researcher Keir Giles publicly shared screenshots of the fraudulent communications, revealing the attackers’ use of spoofed Department of State email addresses in the carbon copy field to enhance legitimacy.
Social Engineering and Persistence Mechanism
The attackers’ methodology centered on a multi-stage social engineering process that began with benign meeting invitation emails containing spoofed State Department addresses.
.webp)
Upon victim response, attackers delivered PDF documents with detailed instructions for accessing a fictitious Department of State cloud environment.
These documents directed targets to create ASPs through legitimate Google Account settings, leveraging the victims’ trust in official-looking communications to bypass traditional security awareness training focused on malicious links or attachments.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
The post Russian Hackers Impersonating as U.S. Department of State to Obtain ASP Passcode appeared first on Cyber Security News.