A sophisticated malware campaign has emerged that exploits legitimate ConnectWise remote access software to create validly signed malicious applications, representing a significant evolution in cybercriminal tactics.
Since March 2025, security researchers have observed a dramatic increase in attacks using what they term “EvilConwi,” a technique that allows threat actors to build custom remote access malware while maintaining the legitimate digital signatures of ConnectWise applications.
The campaign primarily spreads through phishing emails containing OneDrive links that redirect victims to deceptive Canva pages with “View PDF” buttons, ultimately downloading malicious ConnectWise installers.
These attacks have been particularly effective because most antivirus products fail to detect the maliciously configured ConnectWise samples as malware, even as late as May 2025.
.webp)
Victims report experiencing fake Windows update screens and unauthorized mouse movements, indicating active remote connections established by attackers.
G Data analysts identified the threat after investigating multiple user reports on cybersecurity forums, where victims sought help removing unwanted ConnectWise infections.
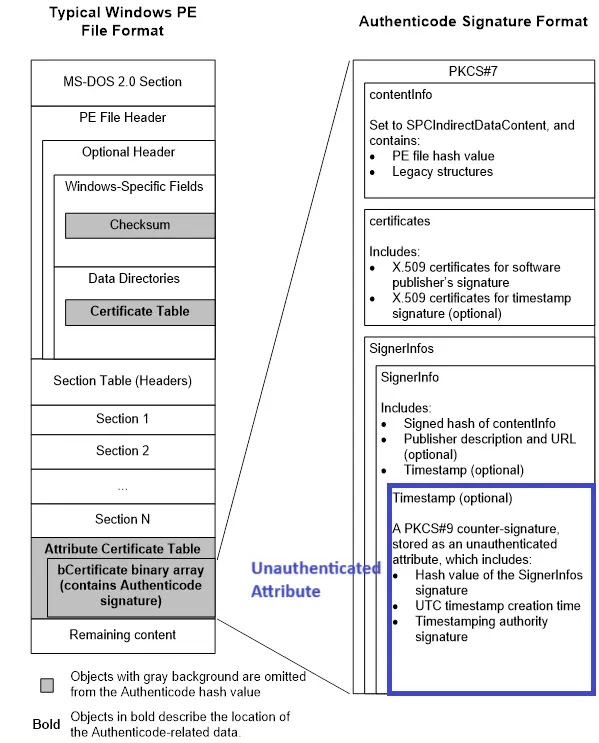
The researchers discovered that threat actors are leveraging a technique called “Authenticode stuffing” to embed malicious configurations within the certificate structure of legitimate ConnectWise installers, allowing them to modify application behavior without invalidating the digital signature.
The malware disguises itself as various legitimate applications, including AI-based image converters, Zoom installers, Microsoft Excel setup files, and Adobe updates.
Once installed, the malicious ConnectWise clients establish persistent remote connections while hiding their presence through disabled system tray icons, suppressed connection notifications, and fake Windows update screens that discourage users from shutting down their systems.
Authenticode Stuffing: The Technical Foundation of the Attack
The core of this attack relies on a sophisticated abuse of the Authenticode signing process through a technique known as “Authenticode stuffing.”
.webp)
This method exploits how Windows validates digital signatures by placing malicious configuration data in unauthenticated attributes within the certificate table, which are excluded from the signature verification process.
When Windows calculates the authentihash to verify a Portable Executable file’s certificate, it deliberately omits certain areas including the certificate table itself and any unauthenticated attributes contained within it.
Threat actors exploit this design by embedding comprehensive configuration data in these excluded sections, effectively creating a legitimate signing mechanism for malware distribution.
G Data researchers developed analysis tools to extract these hidden configurations, revealing the extensive customization capabilities available to attackers.
Their Python-based certificate extraction script demonstrates how threat actors embed critical behavioral modifications directly within the certificate structure:-
import pefile
from asn1crypto import cms
import sys
import os
def dump_certificate_table(file_path, output_dir):
pe = pefile.PE(file_path, fast_load=True)
security_dir_entry = pe.OPTIONAL_HEADER.DATA_DIRECTORY[
pefile.DIRECTORY_ENTRY['IMAGE_DIRECTORY_ENTRY_SECURITY']
]
if security_dir_entry.VirtualAddress == 0:
print("No certificate table found.")
return
cert_table_offset = security_dir_entry.VirtualAddress
cert_table_size = security_dir_entry.Size
cert_data = pe.__data__[cert_table_offset: cert_table_offset + cert_table_size]The embedded configurations include silent installation flags, connection URLs and ports, custom application icons, deceptive window titles, and settings that disable security indicators.
Analysis of malicious samples reveals configurations that replace legitimate ConnectWise branding with Google Chrome icons and fake Windows update messages, while systematically disabling features like system tray notifications and connection wallpapers that would alert users to active remote sessions.
This technique represents a particularly concerning development in malware distribution, as it allows cybercriminals to create fully functional remote access tools using the trusted digital signatures of legitimate software vendors, effectively bypassing traditional security controls while maintaining persistent access to compromised systems.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free tria
The post Threat Actors Abuse ConnectWise Configuration to Build a Signed Malware appeared first on Cyber Security News.