A sophisticated new Android botnet malware called AntiDot has emerged as a significant threat to mobile device security, offering cybercriminals unprecedented control over infected devices.
This malicious software operates as part of a Malware-as-a-Service (MaaS) model, marketed by threat actor LARVA-398 on underground forums as a comprehensive “3-in-1” tool that combines its own loader, packer, and botnet infrastructure into a single dangerous package.
The malware represents a concerning evolution in mobile threats, featuring advanced capabilities including screen recording through Android accessibility service abuse, SMS message interception, and systematic harvesting of application logs to exfiltrate sensitive user data.
.webp)
Campaign activity analysis reveals that threat actors are strategically targeting victims based on specific language preferences and geographic locations, suggesting sophisticated distribution methods likely involving malicious advertising networks and highly tailored phishing campaigns.
Catalyst analysts identified that AntiDot’s operational infrastructure currently encompasses at least 11 active command-and-control (C2) servers managing more than 3,775 infected devices across a minimum of 273 distinct campaigns.
Remarkably, none of these C2 servers appear in public threat intelligence databases, and the associated domain “gates” remain undetected by most commercial security solutions, highlighting the malware’s sophisticated evasion capabilities.
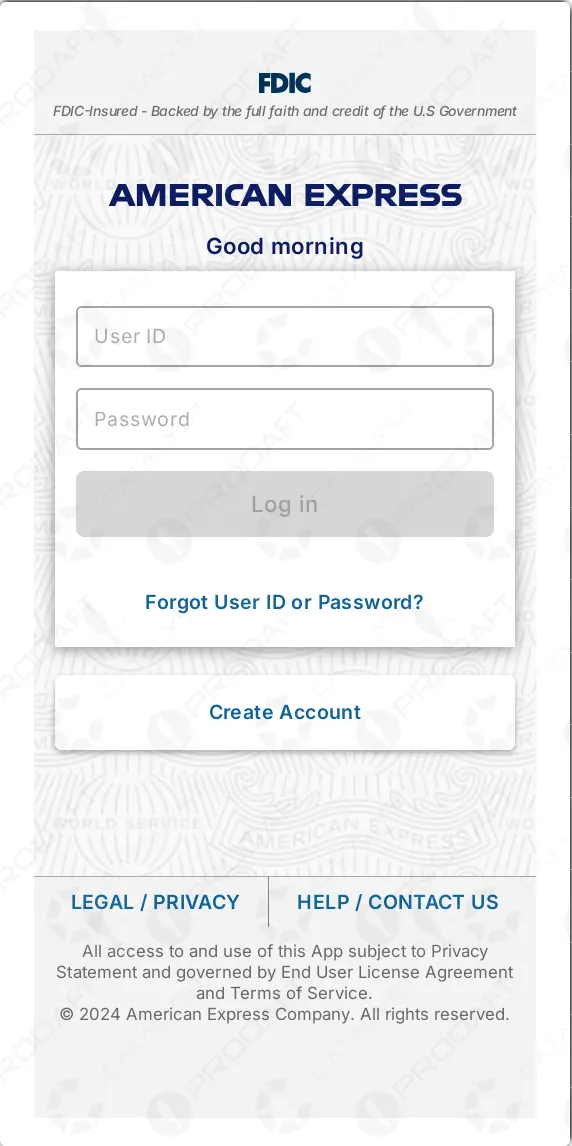
The threat’s scope extends beyond simple data theft, incorporating interface cloning technologies that enable attackers to create convincing replicas of legitimate applications.
This capability allows cybercriminals to conduct overlay attacks specifically targeting cryptocurrency and payment-related applications, though the system supports customizable presets for broader targeting scenarios.
.webp)
Each C2 server typically manages infections from narrow geographic or linguistic demographics, reinforcing the targeted nature of these operations.
The malware’s distribution strategy appears highly flexible, with campaign identifiers following structured patterns such as “1206tv04” and “13TTPT01,” indicating automated generation systems, while others use arbitrary or themed names potentially reflecting specific lures or geographic targets.
Underground forum discussions suggest some dissatisfaction with LARVA-398’s customer support, particularly regarding compatibility with latest Android versions, though this has not diminished the malware’s operational effectiveness.
Advanced Command and Control Architecture
AntiDot’s most concerning aspect lies in its sophisticated command and control infrastructure, which utilizes WebSocket protocols for real-time communication between infected devices and operator panels.
The malware employs a multi-stage infection process, typically delivered as “Update.apk,” which initially displays a deceptive update progress bar while requesting critical accessibility permissions from unsuspecting users.
Once permissions are granted, the malware unpacks and loads encrypted DEX files containing the primary botnet capabilities.
.webp)
The system uses commercial packers to evade antivirus detection, employing obfuscation techniques that significantly complicate both static and dynamic analysis.
The AndroidManifest inspection reveals that numerous class names are absent from the original APK, as these malicious components are dynamically loaded during installation from encrypted files.
The C2 panel operates through MeteorJS framework, maintaining real-time data feeds through WebSocket connections that enable operators to monitor victim statistics and configure overlay targets dynamically.
This architecture supports an extensive command set including device control functions, application management, SMS manipulation, and sophisticated overlay operations that can mimic legitimate application interfaces to steal credentials and financial information.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial
The post AntiDot – 3-in-1 Android Malware Let Attackers Full Control of Compromised Devices appeared first on Cyber Security News.