A sophisticated new social engineering technique called ClickFix has exploded across the cyberthreat landscape, experiencing an unprecedented surge of 517% between the second half of 2024 and the first half of 2025.
This alarming growth has propelled ClickFix to become the second most prevalent attack vector after phishing, accounting for nearly 8% of all blocked cyberattacks according to recent threat intelligence data.
The ClickFix technique represents a cunning evolution in cybercriminal tactics, exploiting users’ familiarity with routine web verification processes to deliver malicious payloads.
Unlike traditional attack methods, ClickFix weaponizes the frustrating but commonplace experience of solving reCAPTCHA challenges, transforming these mundane security checks into dangerous traps.
The attack presents victims with fake error messages or verification prompts that appear legitimate, instructing them to copy and paste seemingly harmless commands to resolve fictitious technical issues.
ESET analysts identified that ClickFix campaigns have rapidly expanded beyond their initial scope, now targeting users across Windows, Linux, and macOS platforms.
The malware’s versatility has attracted a diverse array of threat actors, from cybercriminal groups distributing infostealers and ransomware to sophisticated nation-state actors including North Korea-aligned Kimsuky and Lazarus groups, Russia-aligned Callisto and Sednit, Iran-aligned MuddyWater, and Pakistan-aligned APT36.
This broad adoption demonstrates the technique’s effectiveness across different threat actor motivations and capabilities.
Geographic analysis reveals that ClickFix attacks have achieved global reach, with Japan bearing the brunt of attacks at 23% of all detections, followed by Peru at 6%, and Poland, Spain, and Slovakia each experiencing over 5% of global attack attempts.
The technique first emerged in March 2024 through campaigns documented by Proofpoint, initially deployed by threat groups ClearFake and TA571, but has since evolved into a widespread phenomenon affecting millions of users worldwide.
Infection Mechanism and Social Engineering Tactics
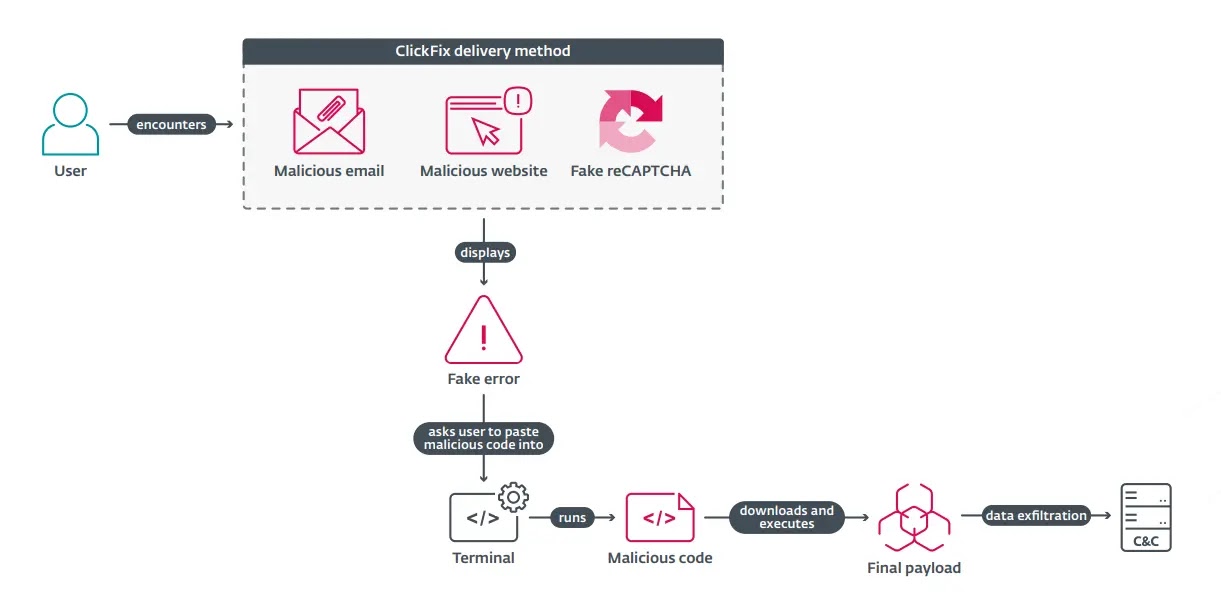
The ClickFix attack chain begins with sophisticated social engineering that exploits users’ conditioned responses to web security prompts.
.webp)
Threat actors create convincing replicas of popular services such as Booking.com, Google Meet, or Microsoft platforms, presenting victims with what appears to be a routine verification step.
The fake interface displays error messages claiming that content cannot be accessed due to technical issues, accompanied by prominent “Fix it” buttons that promise immediate resolution.
When victims click these deceptive buttons, the malware automatically copies malicious PowerShell commands to their clipboard.
The interface then instructs users to open a PowerShell terminal and paste the copied content to “resolve” the fabricated error.
This PowerShell payload serves as the initial stage of a multi-layered attack chain, typically executing commands that download and launch secondary payloads while maintaining the illusion of legitimate system maintenance.
The copied commands often contain obfuscated PowerShell scripts designed to evade basic security detection.
A typical ClickFix payload might include encoded Base64 strings that, when executed, establish persistence mechanisms, disable security features, and initiate communication with command-and-control servers.
The malware employs various “envelopes” or obfuscation techniques to mask secondary payloads, making detection challenging for traditional antivirus solutions that rely primarily on signature-based detection methods.
ESET researchers noted that the attack’s effectiveness stems from its psychological manipulation of user behavior, capitalizing on the prevalence of legitimate verification processes that have trained users to follow copy-paste instructions without question.
This conditioning, combined with the technique’s technical sophistication, has enabled ClickFix to achieve remarkable success rates across diverse target populations and geographic regions.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
The post ClickFix Attack Emerges by Over 500% – Hackers Actively Using This Technique to Trick Users appeared first on Cyber Security News.