Scattered Spider, one of the most sophisticated and persistent cybercriminal groups active today, has focused on their evolution from basic phishing operations to complex multi-stage ransomware campaigns targeting critical infrastructure.
The group’s transition to hypervisor-level attacks and adoption of new ransomware variants represents a significant escalation in both capability and impact, demanding immediate attention from security professionals worldwide.
Scattered Spider (also known as UNC3944, Octo Tempest, 0ktapus, Muddled Libra, and Scatter Swine) has emerged as one of the most dangerous and adaptive threat actors in the current cybersecurity landscape.
Unlike traditional cybercriminal groups that rely heavily on malware and technical exploits, Scattered Spider has perfected the art of social engineering, making them uniquely effective at bypassing even mature security programs.
The group’s recent evolution includes a strategic shift toward targeting virtualization infrastructure, particularly VMware vSphere and ESXi environments, enabling them to deploy ransomware directly from hypervisors and maximize operational disruption.
Their adoption of DragonForce ransomware in 2025, combined with their proven social engineering capabilities, has resulted in successful attacks against major retail chains, airlines, insurance companies, and critical infrastructure organizations across the United States and United Kingdom.
Background and Group Composition
Scattered Spider emerged in May 2022 as a financially motivated cybercriminal collective consisting primarily of native English-speaking young adults and teenagers based in the United States, United Kingdom, and Canada.
The group is believed to be affiliated with a larger underground community known as “The Com” or “The Community,” which has been linked to various criminal activities, including extortion, money laundering, cryptocurrency theft, and SIM swapping operations.
Unlike traditional state-sponsored advanced persistent threats (APTs) or highly technical ransomware groups, Scattered Spider operates as a loose confederation of individual threat actors who collaborate through encrypted communication channels.
This decentralized structure has proven remarkably resilient, allowing the group to continue operations despite multiple high-profile arrests throughout 2024 and 2025.
Key Characteristics and Capabilities
The group’s primary strengths lie in their sophisticated understanding of Western business practices and their exceptional social engineering capabilities.
Their native English proficiency, combined with extensive reconnaissance capabilities, allows them to convincingly impersonate employees and IT personnel during voice-based attacks. This linguistic and cultural advantage has been instrumental in their success against English-speaking targets.
Scattered Spider operates using a “living off the land” (LotL) approach, preferring to abuse legitimate administrative tools rather than deploying custom malware. This methodology significantly reduces their detection footprint while maximizing their ability to blend in with normal network activity.
Evolution of Tactics, Techniques, and Procedures
Historical TTPs (2022-2023)
The group initially focused on SIM swapping attacks and credential theft targeting telecommunications and business process outsourcing (BPO) companies.
Their early campaigns involved broad phishing and SMS phishing (smishing) attempts using organization-specific domains such as “targetsname-sso[.]com” and “targetsname-okta[.]com”.
During this period, their primary monetization strategy involved enabling SIM swapping operations for secondary criminal activities rather than direct extortion. The group demonstrated proficiency in creating convincing phishing domains that closely mimicked legitimate company infrastructure, particularly single sign-on (SSO) portals.
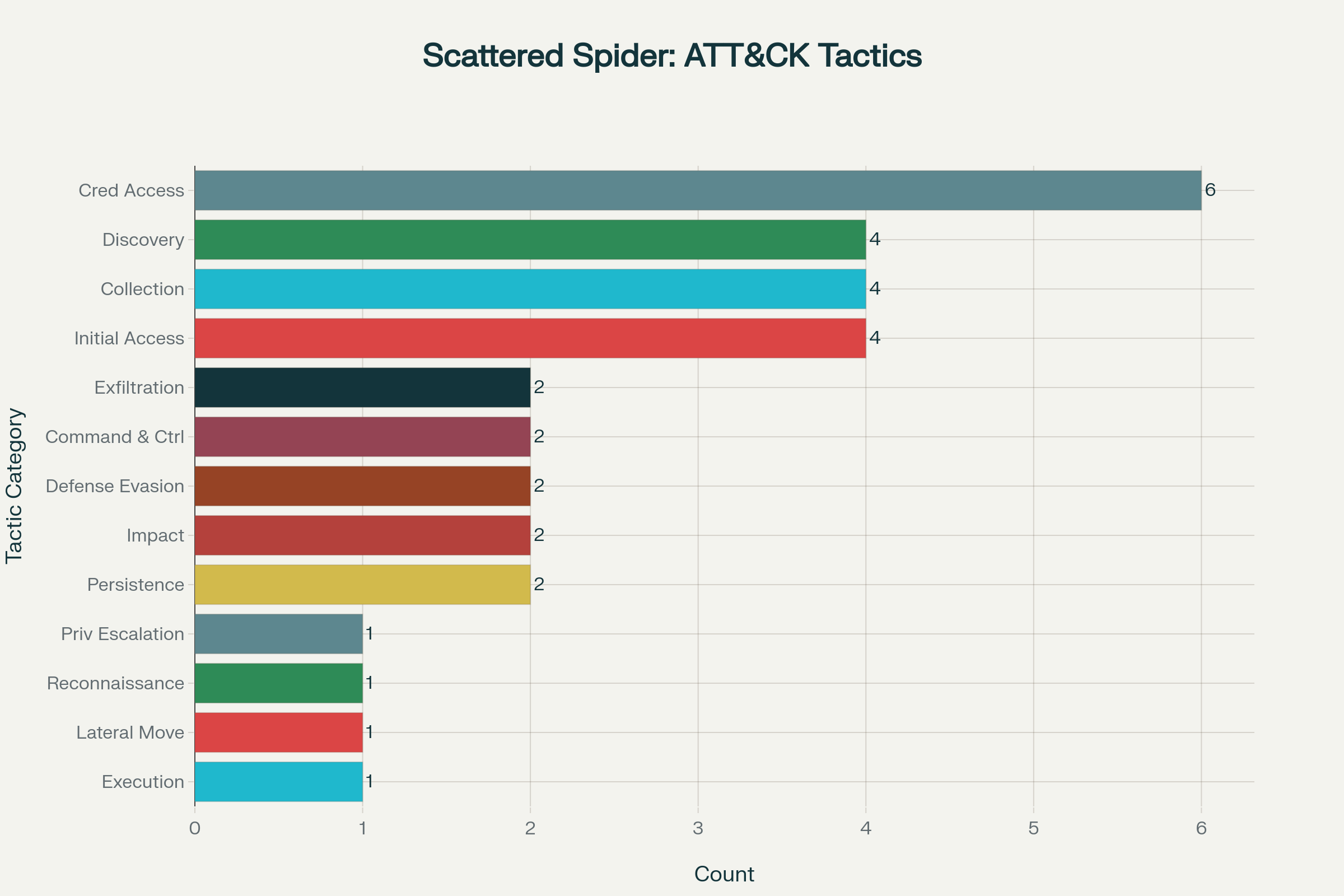
Scattered Spider – Tactics, Techniques, and Procedures (TTPs)
| Tactic | Technique | Procedure/Description | MITRE ATT&CK ID* |
|---|---|---|---|
| Initial Access | Phishing (Spearphishing & Smishing) | Send customized emails or SMS with company-themed lures and fake SSO/Okta portals. | T1566.001 / T1566.002 |
| Social Engineering (Voice Phishing/Vishing) | Impersonate employees or IT staff to convince help desk to reset credentials or MFA tokens. | T1598 | |
| SIM Swapping | Conduct attacks to hijack phone numbers and intercept 2FA/MFA codes. | T1110, T1586.004 | |
| Execution | Legitimate Remote Management Tools | Deploy AnyDesk, TeamViewer, ScreenConnect, TacticalRMM, etc. for persistent remote access. | T1219, T1106, T1569.002 |
| Commercial RATs | Deploy WarZone/AveMaria, RattyRAT for remote access and control. | T1059, T1129 | |
| Persistence | Privileged Account Creation | Create new local or domain admin accounts to retain access after detection. | T1136.002, T1136.001 |
| Abuse of SSO/Federation | Add malicious Identity Providers and sync arbitrary attributes for continued unauthorized access. | T1484, T1550.004, T1078 | |
| Privilege Escalation | Credential Dumping | Use tools like Mimikatz to extract credentials from memory and Active Directory databases (NTDS.dit). | T1003, T1003.003 |
| Hypervisor Compromise (VMware) | Gain access to vCenter; enable SSH on ESXi hosts; reset root passwords for hypervisor-level control. | T1059.004, T1546.008 | |
| Defense Evasion | Living off the Land (LotL) | Use built-in admin tools (e.g., PowerShell, PsExec) to blend malicious activity with legitimate use. | T1218, T1562.001 |
| Proxy Networks & Machine Rotation | Routinely change IPs, device names, and use proxies to mask operations. | T1578, T1090.002 | |
| Credential Access | Raccoon Stealer / VIDAR | Deploy info-stealers for browser and credential data collection. | T1003.001, T1081 |
| Discovery | Cloud Inventory Reconnaissance | Abuse AWS Systems Manager Inventory & scan Snowflake for valuable data assets. | T1538, T1087.004 |
| Lateral Movement | Exploit SSO Federation | Move laterally by using compromised federated identities across cloud and on-prem. | T1550.004, T1021 |
| RMM & VPNs | Use RMM tools and Tailscale VPN to pivot across environments. | T1219, T1071.001, T1090 | |
| Collection | Mass Data Access | Query, collect, and compress large datasets in cloud storage, SharePoint, and network shares. | T1530, T1119 |
| Disk Swap (Domain Controller) | Swap NTDS.dit for extraction of all Active Directory credentials. | T1003.003 | |
| Exfiltration | Cloud Storage (MEGA.nz, AWS S3) | Exfiltrate data via cloud services to minimize detection. | T1567.002, T1041 |
| Impact | Ransomware Deployment (DragonForce) | Encrypt VMware ESXi hosts, backup systems, and business files with robust ransomware capable of hypervisor-level impact. | T1486 |
| Ransom Demands & Extortion | Threaten public leaks and operational disruption to force payment. | T1490, T1657 | |
| Command & Control | Dynamic DNS Domains | Use rapidly changing domains for callback and control infrastructure. | T1071.004, T1583.001 |
| Third-Party Services | Abuse Slack, Teams, Exchange, and social media for in-situ monitoring and C2. | T1102 |
Advanced Social Engineering Operations (2023-2024)
By 2023, Scattered Spider had evolved from broad phishing campaigns to highly targeted, multilayered social engineering operations. Their methodology became increasingly sophisticated, incorporating multiple reconnaissance phases and carefully orchestrated voice-based attacks (vishing).
The group’s social engineering process typically involves several stages: initial intelligence gathering through social media and business-to-business websites, followed by layered phone calls designed to gather password reset procedures, and finally, spearphishing calls to convince IT help desk personnel to reset passwords or transfer MFA tokens.
Their breakthrough came with high-profile attacks against MGM Resorts and Caesars Entertainment in September 2023, which demonstrated their ability to cause massive operational disruption while extracting substantial ransom payments.
The MGM attack alone resulted in over $100 million in losses and showcased their ability to maintain persistent access even during active incident response efforts.
Ransomware Partnerships and Escalation (2024-2025)
The group’s evolution accelerated significantly in 2024 with its adoption of various ransomware-as-a-service (RaaS) platforms.
Initially partnering with ALPHV/BlackCat ransomware operators, they transitioned to RansomHub following ALPHV’s disruption by law enforcement.
Most recently, in 2025, they began deploying DragonForce ransomware, marking another significant evolution in their capabilities.
This transition to ransomware operations represents a fundamental shift in their monetization strategy, moving from SIM swapping enablement to direct double extortion campaigns involving both data theft and system encryption.
Their attacks now regularly result in multi-million dollar ransom demands and have significant impacts on victim organizations’ operational capabilities.
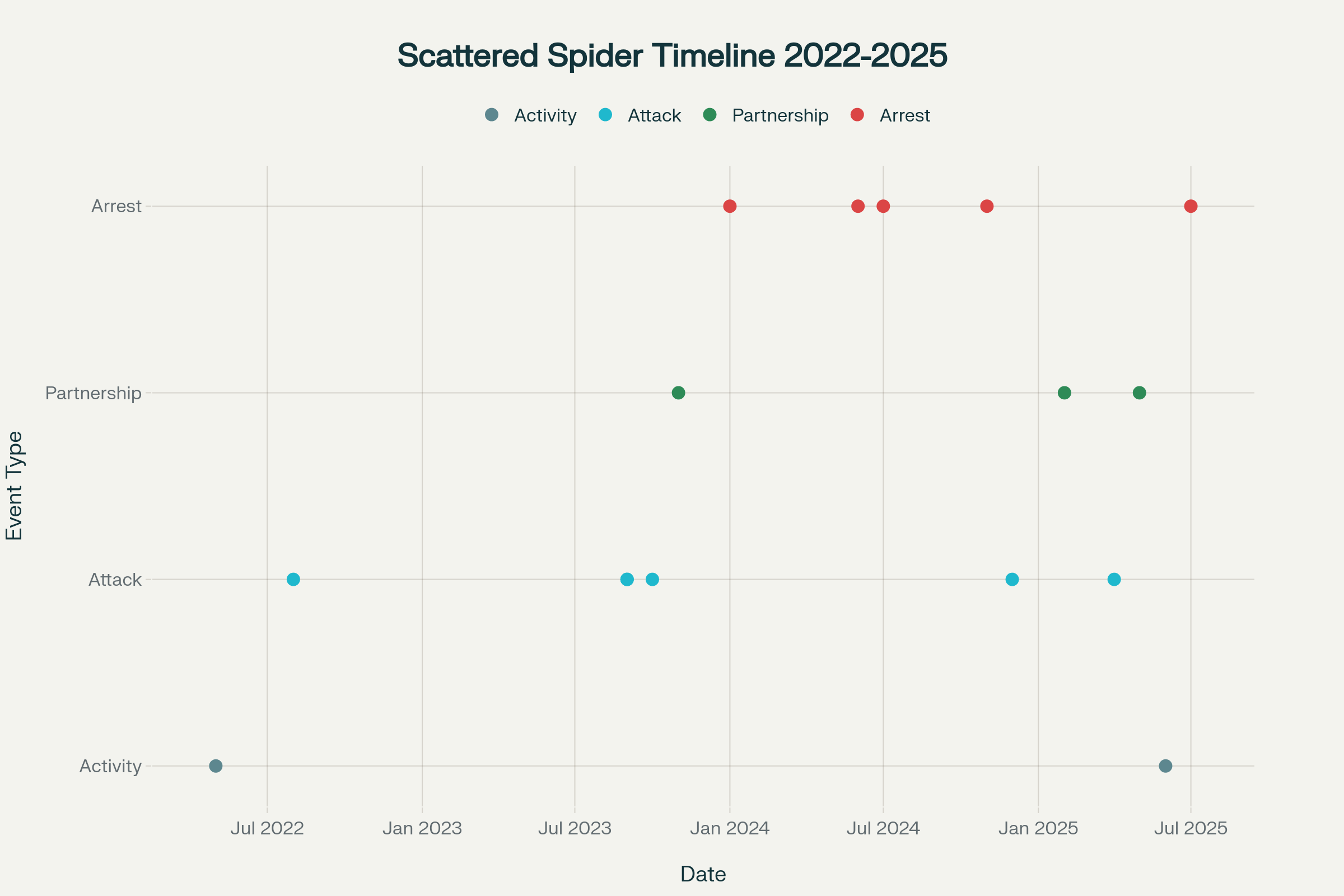
New Tactics and Techniques in 2025
Hypervisor-Level Attacks
One of the most significant developments in Scattered Spider’s 2025 operations is their systematic targeting of VMware vSphere environments, particularly ESXi hypervisors.
This represents a sophisticated evolution that allows them to bypass traditional endpoint detection and response (EDR) tools while maximizing the impact of their ransomware deployments.
Their hypervisor attack methodology follows a consistent pattern: after gaining initial access through social engineering, they pivot from compromised Active Directory environments to VMware vCenter Server Appliances.
Once they control the vCenter management interface, they can enable SSH access on ESXi hosts, reset root passwords, and perform “disk-swap” attacks to extract critical databases like NTDS.dit.
This approach is particularly devastating because it allows attackers to encrypt entire virtual environments from the hypervisor level, rendering in-guest security solutions powerless. A single compromised ESXi server can host dozens or hundreds of virtual machines, making this an extremely efficient attack vector.
Scattered Spider has developed increasingly sophisticated methods for abusing identity and access management systems. Their current techniques include Cross-Tenant Synchronization (CTS) abuse within Microsoft Entra ID environments, which allows them to maintain persistence even after their original access is revoked.
The group has also perfected the abuse of federated identity providers, adding malicious identity providers to victim SSO tenants and activating automatic account linking. This technique allows them to sign into any account by controlling arbitrary values for SSO account attributes, effectively bypassing traditional authentication controls.
Cloud Environment Targeting
Recent campaigns have shown an increased focus on cloud storage environments, particularly targeting Snowflake Data Cloud instances.
The group has been observed running thousands of queries against Snowflake environments to exfiltrate large volumes of data in short timeframes.
This shift toward cloud storage targeting aligns with their broader strategy of maximizing data theft for extortion purposes.
Their cloud operations also include the systematic abuse of Amazon Web Services (AWS) Systems Manager Inventory for lateral movement discovery, as well as the creation of new cloud instances specifically for data collection and exfiltration purposes.
Enhanced Evasion and Persistence Techniques
Scattered Spider has refined their evasion techniques to include consistent use of proxy networks and regular rotation of machine names to hamper detection and response efforts.
They also create fake social media profiles to backstop newly created user identities within victim environments, adding an additional layer of legitimacy to their impersonation efforts.
The group now systematically monitors victim communications through platforms like Slack, Microsoft Teams, and Exchange Online to detect security response activities.
This intelligence gathering allows them to adapt their tactics in real-time and often results in them joining incident response calls to gather information about defensive measures.
Technical Analysis of Tools and Malware
Legitimate Tools Weaponized
Scattered Spider’s tool arsenal consists primarily of legitimate software repurposed for malicious activities. Their remote monitoring and management (RMM) toolkit includes AnyDesk, TeamViewer, ScreenConnect, Teleport.sh, Tactical.RMM, Pulseway, and Splashtop.
These tools provide them with persistent remote access while appearing as legitimate administrative software to security monitoring systems.
For credential extraction and lateral movement, they employ tools like Mimikatz for credential dumping, Ngrok for remote access tunneling, and Tailscale for establishing secure VPN connections.
This approach of using legitimate tools significantly complicates detection efforts, as security teams must distinguish between authorized administrative activities and malicious use.
Malware Arsenal
While the group prefers legitimate tools, they do deploy specific malware families when necessary. Their current malware arsenal includes:
AveMaria (WarZone RAT): A commercial remote access trojan used for persistent system access and reconnaissance. This tool provides comprehensive remote control capabilities and is difficult to detect due to its commercial legitimacy.
Raccoon Stealer: An information stealer specifically designed to harvest login credentials, browser histories, cookies, and other sensitive data. The malware is particularly effective at gathering the authentication artifacts needed for their social engineering campaigns.
VIDAR Stealer: Another credential harvesting tool that focuses on extracting stored passwords, browser data, and cryptocurrency wallet information. This malware complements their broader credential theft strategy.
RattyRAT: A newer addition to their arsenal, this Java-based remote access trojan is used for persistent, stealth access and internal reconnaissance activities. Its Java-based architecture makes it particularly suitable for cross-platform operations.
DragonForce Ransomware
The group’s adoption of DragonForce ransomware in 2025 represents a significant escalation in their destructive capabilities. DragonForce is a sophisticated ransomware variant that targets both traditional IT infrastructure and virtualized environments, with particular emphasis on VMware ESXi servers.
The ransomware employs robust encryption combining RSA and AES algorithms to lock files and can encrypt a wide range of targets, including network-attached storage (NAS) devices, databases, and backup systems.
Notably, DragonForce has developed specific capabilities for encrypting VMware environments, allowing attackers to disable entire virtual server farms with a single deployment.
Indicators of Compromise and Detection
Network Indicators
Certainly! Here is a comprehensive table summarizing the Indicators of Compromise (IoCs) and Detection related to Scattered Spider operations, including file hashes, domain patterns, exfiltration methods, tool artifacts, and behavioral detection clues.
Scattered Spider – Indicators of Compromise & Detection
| Indicator Type | Example / Value | Detection Notes / Usage Context |
|---|---|---|
| Network Domain | targetsname-cms[.]com, targetsname-helpdesk[.]com, oktalogin-targetcompany[.]com | Predictable themes; used in phishing infrastructure; usually ephemeral before abandonment. |
| File Hash | DragonForce (SHA256): 1250ba6f25fd60077f698a2617c15f89d58c1867339bfd9ee8ab19ce9943304b | Associated with ransomware deployment; match across endpoints and backups for impact assessment. |
| File Hash | DragonForce (SHA1): e164bbaf848fa5d46fa42f62402a1c55330ef562 MD5: d54bae930b038950c2947f5397c13f84 | File-level detection of DragonForce Ransomware. |
| Malware Artifact | Winupdate.exe (Go-based), FileSeek.exe | Found at C:\Users\Public\Documents\ or C:\Windows\system32; used for data exfiltration/discovery. |
| Exfiltration | Use of MEGA.nz, Amazon S3 | Detect outbound file uploads or connections to cloud storage providers from internal hosts. |
| Tool Install | AnyDesk, TeamViewer, ScreenConnect, TacticalRMM, Splashtop | Unusual RMM software installs outside IT management activity. |
| Behavioral | Mass file access in SharePoint, network shares, or sudden data access spikes | Indicates staged data collection for exfiltration or extortion. |
| Behavioral | Anomalous password resets, especially for privileged or admin accounts | Often follows vishing or social engineering calls to help desk. |
| System Change | SSH enabled on ESXi hosts; root password resets | Indicates possible lateral movement/persistence in VMware environments. |
| C2 Infrastructure | Dynamic DNS domains, rapid domain/IP rotation | Monitor DNS requests and outbound connections to high-risk, short-lived domains. |
| Cloud Patterns | Spikes in Snowflake queries, new/excessive AWS SSM inventory usage | Detect excessive database queries or misused cloud inventory tools. |
| Persistence | New local/domain admin accounts, modifications to Identity Providers in SSO configs | Often created post-compromise for long-term attacker access. |
- Monitor for installation and execution of remote access and file exfiltration tools.
- Alert on suspicious file hashes and unknown binaries in common or system directories.
- Implement DLP and network monitoring for large outbound file transfers, especially toward cloud platforms like MEGA.nz and S3.
- Investigate anomalous help desk activity and privilege escalations, particularly those performed outside of change control windows.
- Audit VMware configuration changes, especially enabling SSH or bulk VM operations.
- Watch for behavioral anomalies in user file access, query rates, and cloud service usage.
The following network indicators have been associated with Scattered Spider operations:
Domain Patterns: The group continues to use predictable domain naming conventions for their phishing infrastructure. Current patterns include “targetsname-cms[.]com”, “targetsname-helpdesk[.]com”, and “oktalogin-targetcompany[.]com”. These domains are typically used for brief periods and then abandoned.
Exfiltration Infrastructure: MEGA.NZ has been identified as a primary exfiltration platform used by the group, along with various US-based data centers for staging stolen information. The group also utilizes cloud storage services like Amazon S3 for data exfiltration operations.
File-Based Indicators
Several file-based indicators have been identified in recent Scattered Spider campaigns:
Certainly! Below is a detailed table summarizing the key tools (both legitimate and malicious) used by the Scattered Spider threat actor during campaigns observed through 2025. This includes remote access, credential dumping, information stealing, and exfiltration utilities, along with their typical usage context.
Scattered Spider – Tools Used
| Tool Name | Category | Description / Usage Context |
|---|---|---|
| AnyDesk | Remote Management | Used for persistent remote access and control of compromised systems. |
| TeamViewer | Remote Management | Provides remote desktop capability for post-compromise operations. |
| ScreenConnect | Remote Management | Enables covert lateral movement and remote access via legitimate RMM channels. |
| TacticalRMM | Remote Management | Utilized for automated administration and maintaining persistence. |
| Splashtop | Remote Management | Deployed for unobtrusive, encrypted remote sessions to victims. |
| Pulseway | Remote Management | Assists in stealthy persistence and post-exploitation system management. |
| Teleport.sh | Remote Management | Used for scalable, secure remote access and privileged session management. |
| Tailscale | VPN / Connectivity | Establishes secure, peer-to-peer VPN tunnels between attacker and victim infrastructure. |
| Ngrok | Tunneling | Exposes internal services to the internet through reverse tunnels for C2/backdoor use. |
| Mimikatz | Credential Dumping | Harvests credentials from Windows memory, including NT hashes and Kerberos tickets. |
| Raccoon Stealer | Info Stealer | Steals browser-stored credentials, cookies, autofills, and other sensitive data. |
| VIDAR Stealer | Info Stealer | Focused on extracting account credentials, browser data, and crypto-wallet secrets. |
| AveMaria (WarZone RAT) | Remote Access Trojan | Enables stealthy, persistent RAT capabilities for ongoing C2 and internal recon. |
| RattyRAT | Remote Access Trojan | Java-based cross-platform trojan for persistence and reconnaissance. |
| FileSeek.exe | File Discovery | Searches local and network file systems to identify valuable data for exfiltration. |
| Winupdate.exe | Exfiltration Tool | Custom Go-based utility to stage and exfiltrate stolen files. |
| PowerShell | Living-off-the-Land | Used for in-memory execution of payloads, recon, lateral movement, and admin tasks. |
| PsExec | Living-off-the-Land | Lateral movement and remote code execution across Windows environments. |
| DragonForce Ransomware | Ransomware | Encrypts files, VMs, backup systems, and causes operational disruption. |
| MEGA.nz | Cloud Storage | Used for exfiltrating stolen data out of victim environments. |
| Amazon S3 | Cloud Storage | Alternate destination for exfiltration of sensitive data artifacts. |
These tools empower Scattered Spider to conduct stealthy, multi-stage intrusions, blending legitimate system administration activities with highly targeted attacker objectives. Let me know if you’d like the tools mapped to specific attack stages, or if you need deeper technical indicators for detection!
DragonForce Ransomware Hashes:
- SHA256: 1250ba6f25fd60077f698a2617c15f89d58c1867339bfd9ee8ab19ce9943304b.
- SHA1: e164bbaf848fa5d46fa42f62402a1c55330ef562.
- MD5: d54bae930b038950c2947f5397c13f84.
Custom Tools:
- Winupdate.exe: A GoLang-based data exfiltration tool found at C:\Users\Public\Documents\Winupdate.exe and C:\Windows\system32\Winupdate.exe
- FileSeek.exe: File discovery tool used for identifying exfiltration targets.
Behavioral Indicators
Key behavioral indicators include:
- Unusual help desk activity, particularly password reset requests for privileged accounts.
- Sudden installation of remote access tools on endpoints.
- Anomalous login patterns, ei hosts.
- Creation of new administrative accounts in Active Directory.
Defensive Strategies and Countermeasures
Identity and Access Management Hardening
Given Scattered Spider’s focus on identity-based attacks, organizations must implement comprehensive identity security measures. This includes mandatory deployment of phishing-resistant multi-factor authentication (MFA) using FIDO/WebAuthn standards or PKI-based solutions across all critical systems.
Organizations should also implement strict conditional access policies that consider device compliance, geographic location, and user behavior patterns. Regular audits of privileged account access and automated alerting for any changes to administrative groups are essential defensive measures.
Help Desk Security Procedures
Help desk operations represent a critical vulnerability that Scattered Spider consistently exploits. Organizations must implement enhanced verification procedures for password resets and account modifications, particularly for privileged accounts.
This should include out-of-band verification using predetermined contact methods and supervisor approval for high-privilege account changes.
Staff training programs should specifically address social engineering tactics used by sophisticated threat actors, including voice-based attacks that may use accurate personal information about employees.
Help desk personnel should be trained to recognize the behavioral indicators of social engineering attacks, such as unusual urgency, requests to repeat questions, or long pauses during verification processes.
Virtualization Infrastructure Security
Protection of VMware vSphere environments requires specialized security measures that go beyond traditional endpoint protection.
Organizations should implement strict access controls for vCenter Server environments, including dedicated administrative workstations and network segmentation that isolates virtualization management from general corporate networks.
ESXi hosts should be configured with hardened security baselines that disable SSH access by default, implement certificate-based authentication, and utilize VM encryption where possible.
Regular monitoring should be established for any configuration changes to virtualization infrastructure, with automated alerting for SSH enablement or root password resets.
Cloud Security Enhancements
Given the group’s increased focus on cloud environments, organizations must implement comprehensive cloud security posture management (CSPM) solutions.
This includes regular assessment of cloud storage permissions, implementation of data loss prevention (DLP) controls for cloud platforms, and enhanced monitoring of unusual query patterns against cloud databases.
Snowflake and similar cloud data platforms should be configured with strict access controls, query monitoring, and automated alerting for unusual data access patterns. Organizations should also implement network-based monitoring to detect large-scale data exfiltration attempts.
Detection and Response Capabilities
Effective detection of Scattered Spider activities requires behavioral analytics capabilities that can identify the subtle indicators of their living-off-the-land approach.
Security operations centers should implement user and entity behavior analytics (UEBA) solutions capable of detecting anomalous patterns in administrative tool usage and account access.
Endpoint detection and response (EDR) solutions should be configured to monitor for the execution of legitimate tools in unusual contexts, such as remote access software launched from unexpected processes or locations. Network monitoring should focus on identifying the use of tunneling tools and unusual outbound communications patterns.
Scattered Spider represents a fundamental shift in the cybercriminal landscape, demonstrating that sophisticated social engineering combined with deep understanding of enterprise infrastructure can be more effective than advanced malware or zero-day exploits.
Their evolution from SIM swapping enablement to full-scale ransomware operations, combined with their adoption of hypervisor-level attack techniques, positions them as one of the most dangerous threat actors currently active.
The group’s resilience in the face of multiple law enforcement actions and their continued innovation in attack methodologies suggest they will remain a significant threat for the foreseeable future.
Their influence on the broader cybercriminal ecosystem is already evident, with other threat groups adopting similar social engineering techniques and targeting strategies.
Organizations must recognize that traditional perimeter-based security models are inadequate against threats like Scattered Spider.
The future of cybersecurity defense lies in comprehensive identity governance, advanced behavioral analytics, and security architectures that assume compromise rather than attempting to prevent all intrusions.
As Scattered Spider continues to evolve and potentially influences other threat actors to adopt similar techniques, the cybersecurity community must prepare for an era where the weakest link is not technical infrastructure, but human trust and organizational processes.
The most effective defense against such threats requires a fundamental reimagining of security architectures, with identity, behavior, and trust verification at the center of every security decision.
Find this coverage helpful! Follow us on LinkedIn and X to Get More Instant Updates.
The post Scattered Spider Threat Actor Profile – New Tactics, Techniques, Procedures and IoCs appeared first on Cyber Security News.